Building Cyber Resilience Through Security Awareness

Cybersecurity is something that is being talked about everywhere. Right from news, social media, and the agenda of many boardroom meetings, it has grown topically from being a buzzword to a complex challenge that organizations need to address in a structured manner. It is not uncommon for organizations to invest heavily in securing their digital perimeters and systems by deploying various types of security technologies that can be used to identify, prevent, and respond to mitigate cyber-attacks.
Although organizations, especially large ones, implement such varied technologies ranging from Next-Generation Firewalls to Data Leakage Prevention along with other sophisticated tools and operations and supposedly proclaim to have state of the art or ‘bank grade’ security, we still get to know about how the very same organizations suffered a data breach. What one wonders is, therefore, despite having various checks and balances in place, compliance to international standards, and best practices, how is it that data breaches still plague many organizations globally?
To find a definitive answer with less room for guesswork, let’s look at the below statistics from the Baker Hostetler Data Security Incident Response Report, which documents the analysis of over 950 incidents the firm helped manage in 2019.
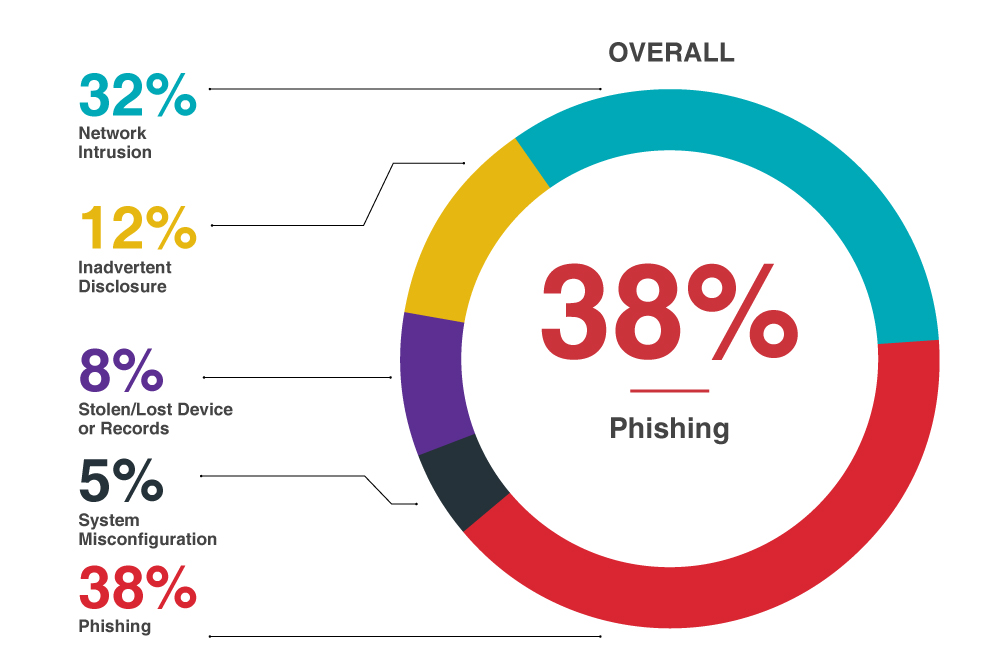
Looking at the overall incidents, it is peculiar to note how a significant portion of those breaches can be attributed to Phishing/Hacking/Malware and Employee Action/Mistake. For Phishing attacks to succeed, the victim involved needs to commit a human error by failing to recognize the red flags of a fraudulently crafted email that is meant to convince and compel the targeted victim to respond in an almost knee jerk reaction, which ultimately results in a compromise- i.e., either the victim ends up disclosing sensitive information like passwords or lands on to a page which launches a malware. The malware, in turn, aims to compromise the victim’s system and install malicious programs which can further gather sensitive data or allow a hacker to control the system and wreak havoc remotely.
In more recent times, the Twitter breach revealed how some of the world’s most well-known celebrities and brands, including high profile users such as Barack Obama, Elon Musk, and Apple, found themselves in a position where they could barely do something than watch in dismay as the hackers continued a rampage to post misleading tweets from the compromised accounts and broadcast messages to promote a bitcoin scam. Twitter confirmed that the perpetrators had gained access to its internal administrative tools, which enabled them to gain access to the account level settings that enabled them to reset passwords by maliciously modifying the associated email addresses with the attackers’ arbitrary email addresses for mail confirmation and thereby initiate the password reset and gain access to the accounts which allowed them to post the tweets directly.
What’s important to note here is the root cause or reason behind the hackers succeeding in this breach was a social engineering attack that was well coordinated and enabled the attackers to successfully manipulate Twitter employees and use their credentials to access Twitter’s internal systems. (See below snapshot from an official statement made by Twitter on their website):
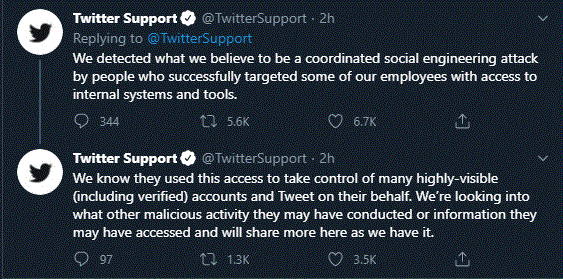
Social engineering is a term that refers to various malicious activities which are performed by tricking or manipulating people into performing actions or making mistakes that allow hackers access to the targeted systems or giving away sensitive information which the hackers can use for furthering their attack. Thus, the case of the Twitter breach, which occurred in 2020, very clearly adds up and validates the statistics analyzed in the above-quoted report.
What makes this breach more vehement is that the attack vectors used allowed the hackers to bypass even the multifactor authentications set by the affected users whose accounts were compromised. Thus, the next time one reads or comes to know about setting a 2FA or MFA to secure their accounts from hackers, the case of the Twitter breach will ring a bell and remind you how there’s no sure-shotted method or a silver bullet when it comes to securing your digital assets.
So, the question is, what really can help address such onslaughts by cyber attackers? And possibly provide a reasonable way to fall back and count on to defend against such threats?
The correct answer to this question would address the root cause of the breach. For instance, if an organization successfully established a robust culture for cybersecurity awareness that included acclimatizing employees to attempts of social engineering and prevented them from falling prey and giving away their credentials, this, in turn, could probably prevent them from being the weakest links that break the security chain, giving way to a mega breach. Thus, the solution to the challenges imposed by Cyber Threats is not always something that is limited to technology solutions and tools alone but is one that looks at organizations and individuals overall as humans, who are prone to making an error, and who also have the potential to be conditioned and trained not to make them in the first place.
Having a high degree of Cyber Resiliency is vastly dependent not just on the technology and processes that organizations have in place but also on the people aspect, which needs to be investigated and addressed. Thus, investing in a Security Awareness Program that has been built by considering the various business operations and human interactions involved in them along with the probable impacts that points of failure in the chain can cause the starting ground for developing a plan that aims to equip crucial users and especially administrators with awareness. This can save the day when it comes to one of the worst breaches of the decade, like the one that affected Twitter. However, Easier said than done, implementing a cybersecurity culture is itself very complex and essentially involves building not just the relevant expertise within a Cyber function but champions or representatives across the enterprise as ambassadors, testing out the awareness of employees through simulated assessments mimicking a real-world attack and constant education that measures how the knowledge of employees improves over time to determine if the organization has a succeeded to build a Human Firewall that actually works!
~Arun Ramakrishnan, Former IS Compliance Officer and Cyber Security Manager at Reserve Bank Information Technology Pvt Ltd (ReBIT)
Did you know that 3.5 million cybersecurity jobs opportunities are slated to be created by the end of 2025? Be a part of this in-demand industry when you upskill with cybersecurity courses at Emeritus India. Gain practical knowledge of via courses in cybersecurity taught by top university faculty and cybersecurity practitioners.


